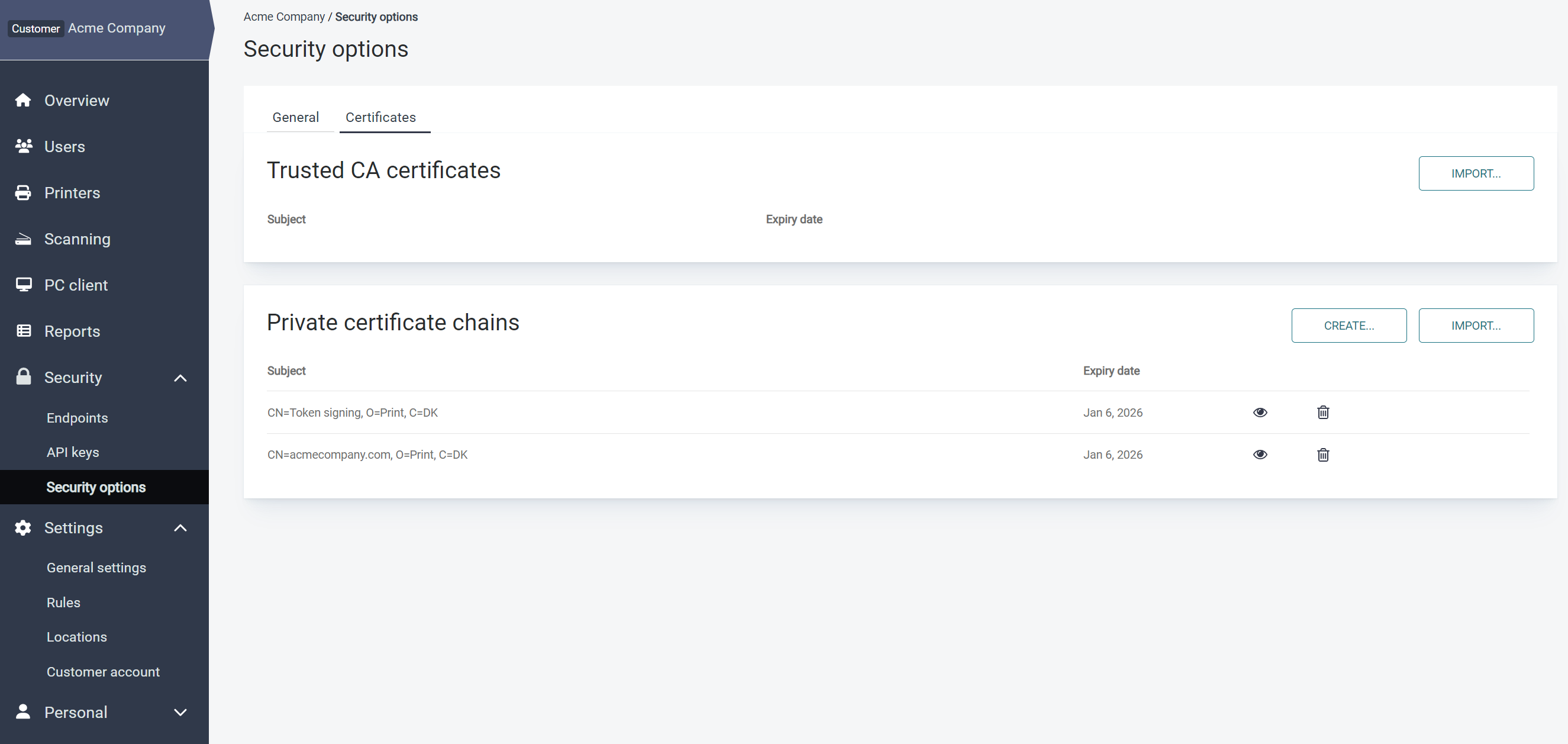
The Certificates tab allows you to import or create valid SSL certificates for a Vendor or Customer account for use in the various interfaces, including PMC Web UI, APIs, IPP print, and embedded terminal communications.
Trusted valid SSL certificates are required for HTTPS/IPPS printing from PMC Client.
Trusted CA certificates
If the vendor or customer account are their own Certificate Authority (CA) and issue certificates for domain controllers, mail servers etc, those CA certificates can be imported to PMC for LDAPS and similar.
Export the certificates from the remote server to PEM or DER format, and click Import to import the trusted certificate.
The PEM file format can contain multiple certificates in a chain. If this is the case, only the last certificate in the chain (typically the CA certificate) will be imported. During the import process, the certificate is validated to ensure it represents a valid Certificate Authority (CA). The import will fail if the certificate does not represent a CA (i.e. if it is an entity certificate).
Private certificate chains
To enable valid trusted SSL connections from PMC Client to the PMC server, either the PMC Web UI in a Web browser, API connections, IPP printing, or in embedded terminals, import a valid SSL certificate chain in PFX or PKCS12 format.
These formats include both public and private keys required for a server to create the encrypted connection. Certificates without the private key would be ignored during import.
When importing Private certificate chains, both the key pair and the keystore file has to be password protected with the same password.
The certificate chain should contain a valid path from the server certificate to the trusted certificate on the clients.
The following criteria must be matched to be able to import the private certificate chain:
-
If the SAN (Subject Alternative Names) are specified, they will be verified against the domains defined in the account.
-
If SAN are empty, CN (Common Name) will be verified against the domains defined in the account.
-
If both SAN and CN are empty, the certificate import will fail.
-
Verification is done as follows:
-
All the DNS names specified in SAN or CN must match at least one of the domains defined in the account.
-
The DNS name may contain a wildcard "*" to allow subdomains (e.g., "SAN=*.test.com" will be valid for the account domain "test.com").
-
It is not possible to import certificates for subdomains (e.g., "SAN=my.test.com" will fail for the account domain "test.com"). However, if you plan to use this subdomain, you can define it in the account information.
-
IP addresses in the SAN are filtered out of the validation; only DNS names are being validated. If the SAN contains only IP addresses, it will be considered empty.
-
Generating certificate chains
Instead of importing a trusted certificate chain, you can generate it using the default PMC CA certificate as an issuer. Certificates can be generated for two purposes: TLS server security and token signing. When generating a TLS certificate, select in the drop-down list the domain name to which this chain will be generated. Embedded clients will then be able to connect to this domain name without warning.
For TLS security, creating a self-signed certificate chain is not recommended and should only be used for test purposes. For proper transport layer protection, a trusted certificate chain created by a trusted certificate authority must be imported.
Generating a certificate chain for token signing
Some external clients require an authorization token when calling PMC public API functions. The token is only issued when there is a signing certificate chosen in the account's PKI settings. By default, each newly created account has a special signing certificate chain created which is also set as a default signing certificate in the PKI settings. It is possible to re-generate it manually or choose another certificate (e.g., import a trusted chain) for signing purposes.