-
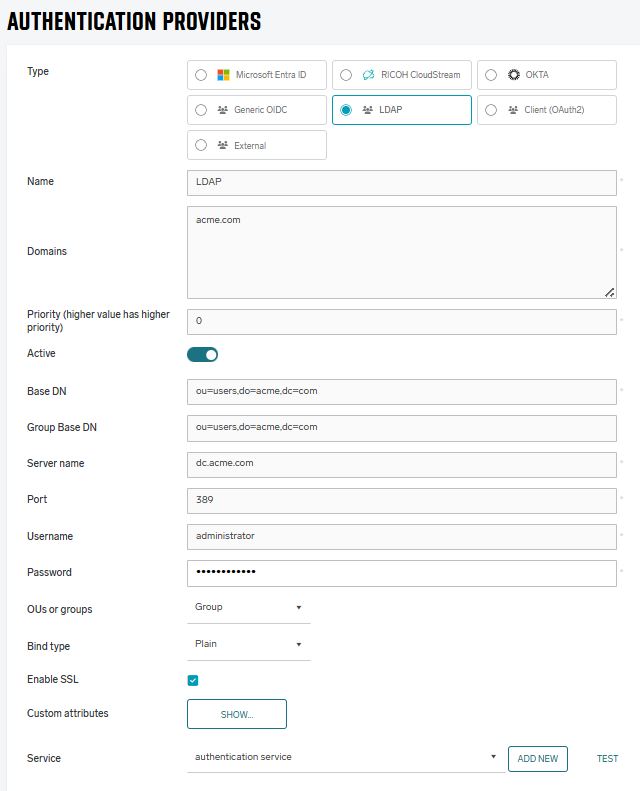
Name – An internal name used for identifying the particular authentication provider configuration. Should be prefilled with the selected Type.
-
Domains – The domain names of the authenticating users. Add here the domain aliases that the users can use to log in. At least one domain in the list should match the domain part of the fully qualified username. If strict domain validation is disabled, PMC will attempt to authenticate the user with all domains in the list when the username does not contain any domain, in the order defined in the list. If strict domain validation is enabled or the username contains a domain, PMC will attempt to authenticate only with the domain in the credentials.
For example, to allow user john.doe@acme.com to log in via this Authentication provider, enter the acme.com domain here.
-
Priority – A number that determines the order in which authentication providers will be called until one succeeds. Higher-priority providers will be called first.
-
Active – If enabled, this authentication provider will be used for authentication. If disabled, this authentication provider will not be searched.
-
Base DN – The point in the LDAP where searching will begin. Will apply to both user and group searching, if Group Base DN is empty.
-
Group Base DN – Possible to specify another starting point for LDAP searching for groups. If omitted, the Base DN is used for group search.
-
Server name – The actual address (DNS, hostname or IP) of the LDAP server to which PMC Authentication Service will connect to search.
-
Port – Port used for the LDAP service, typically 389 for non-SSL and 636 for SSL.
-
Username – Username used to connect and search in the LDAP.
-
Password – Password used to connect and search in the LDAP.
-
OUs or groups – Choose how to identify groups, for access control management, default is “Groups”.
-
Bind type – Whether to bind with Plain connection, MD5 digest, or Kerberos.
-
Enable SSL – Whether connection to LDAP should use SSL encryption.
-
Custom attributes – Expand custom attributes to change the LDAP attributes in which username, card ID’s, ShortID’s and similar are stored.
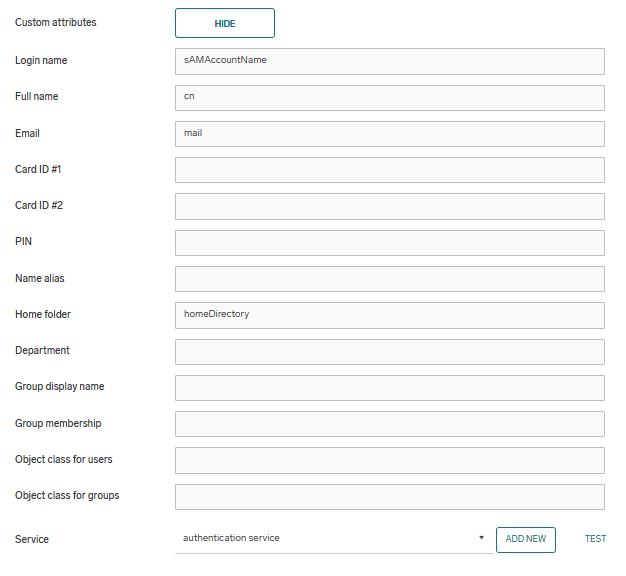
When using the Strict domain validation feature, make sure to set the Login attribute to userPrincipalName.
Service – Which Authentication Service will communicate to this LDAP server. If no service is created, it can be added using the Add button.
Note. If you have multiple Active Directory servers, point authentication to the primary domain.